Knowledge
As overwhelming as an office redesign or move can be, having the right information will often ease any worries and prove crucial to your project’s success.
We’ve collated the most useful facts, resources and opinions to guide you, surprise you and inform you.
To complement our progressive sustainability agenda and further support our clients in minimising the environmental impacts of their moves and changes, we pleased to launch our new carbon neutral relocation service.
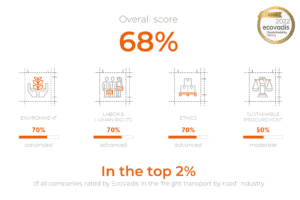
Crown Workspace are delighted to have been awarded gold EcoVardis sustainability rating in their recent assessment by the leading business sustainability monitoring service.
Latest
In this blog, we delve into workplace consultancy, exploring the intricacies of workplace change and space utilisation strategies and their profound implications for businesses.
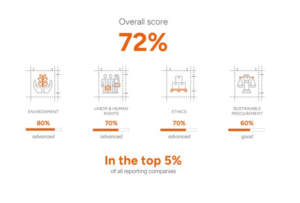
Sustainability remains a top business priority for Crown in the UK & Ireland and globally; we are therefore delighted to have launched our 2023 UKI Sustainability Report!
Crown are delighted to announce that we have been awarded Gold by EcoVadis in 2024 for the second time, reflecting our commitment to and progress in becoming a responsible business.
We supported both Landaid and the YMCA with cardboard boxes for their annual sleepout events. We were incredibly pleased to deliver 1,100 boxes as well as bring along a group of volunteers to the YMCA event.
Crown UK&I are incredibly pleased to have maintained a B score in the ‘Management’ band with CDP this year. This demonstrates our co-ordinated action on climate change issues and reflects our continued progress against an ambitious and holistic sustainability strategy implemented across our UK&I brands.
In our latest blog, we take a look at the 7 key carbon initiatives Crown has implemented so far as we strive towards achieving net-zero emissions.
As businesses evolve and adapt to new challenges, the significance of creating an inspiring workplace environment cannot be overstated. In this blog I look at my top 5 benefits of having an office fit-out.
What are five ways to stay ahead of the curve, retaining employees and attracting new talent in the process? Read our latest blog now!
The world of work is a very different place in 2024, however many people are still talking about finding their way back to “normality”. Read our latest blog to find out more!
Growing the business might mean adding people, but space planning can help you think critically about the space people need to work productively. Read our latest blog today!
In this blog Jacqueline Bird, Head of Move and Change Management, evaluates the many pros and cons of hybrid working, and how to strike a balance in your organisation.
Our Head of Sustainable Development Ann Beavis spoke at the Workplace Trends conference last month, sharing her thoughts on green skills and circular economy thinking within the workplace. Read more!